Efficiency vs. Security?
Staying ahead of the competition requires your company to run with maximum efficiency, with each department working in tandem to address your clients’ needs as fast as possible. But often short-term efficiency gains are achieved at the expense of cybersecurity and compliance with government regulations. As the SolarWinds breach demonstrated, one company’s cyber risk can cause rippling economic and national security implications. Security breaches often slow business down, incurring regulatory fines, and the resulting reputational damage and lost business undermine the bottom line in a big way.
In order to simplify the implementation of security measures in private organizations, the National Institute of Standards and Technology (NIST) developed the Cyber Security Framework in 2014. NIST CSF is a voluntary policy framework of computer security guidance developed in collaboration with private sector organizations that describes how companies can assess and improve their ability to prevent, detect, and respond to cyberattacks. While there is no ironclad way to completely eliminate cybersecurity risk, the framework can help companies create a step-by-step game plan on how to protect themselves against hackers, malware, and other threats.
NIST CSF Basics
The Cyber Security Framework’s three main components are the Core, Profiles, and Implementation Tiers:
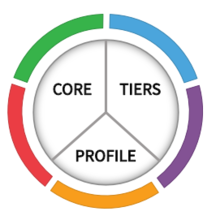
The Core: This component lays out the baseline standards and primary guiding principles of a healthy cybersecurity posture. The Core applies to pretty much any company.
Profiles: Profiles component in the Cyber Security Framework aligns each organization’s unique security requirements with their business objectives, accounting for resources they have at their disposal to achieve security goals. Profiles help organizations create a roadmap to prioritize necessary changes to their security practices without unnecessary business disruption.
Implementation Tiers: NIST CSF’s implementation tiers help organizations compare their current posture with security best practices. The four tiers are:
1. Partial: If this is your company, it means you are dealing with risks as they present themselves, like a cybersecurity edition of Whack-a-Mole. As one might guess, not the best place to be, but a LOT of companies are in this tier.
2. Risk Informed: Your organization has risk management processes set up, but there are no standardized, repeatable, company-wide measures in place, which leaves lots of entry points for cyber threats.
3. Repeatable: If this is your company, congratulations. You have standardized, company-wide processes in place to minimize the risk of cyber threats. But while this is a big accomplishment, but, to fully protect your organization, your cybersecurity processes need to also be…
4. Adaptive: Far too few organizations can claim this gold star. This NIST CSF tier designates an organization whose security practices are not only embedded into company culture, but also designed to proactively adapt to changes both within and outside of the organization. Rather than merely following static security rules, the organization has processes with built-in mechanisms to accommodate change both in technology, business goals, and threat landscape.
Simplifying Governance, Risk, & Compliance
Effective Enterprise Architecture solutionscan help companies map out their technology structure and processes to both pinpoint where compliance breakdowns are occurring and also help create a Governance, Risk, and Compliance roadmap to prevent those breakdowns from happening in the future. With a complete view of your organizational structure, you can standardize security practices according to NIST CSF recommendations. And by seeing how each segment of your company affects all of the others, you can adapt your security practices to changes in your organization as well as an ever-evolving menagerie of threats.




.png)